[
{
"id": "...","name":"UserA","display_name":"User A","visibility":"SHARABLE", [...],
"extended_properties": null,
"extended_preferences": null,
"user_parameters": null,
"access_control_properties": {
"0": {
"ALL": {
"filter_rules": [
{
"column_name": "Region",
"operator": "IN",
"values": [
"West"
]
},
{
"column_name": "state",
"operator": "EQ",
"values": [
"california"
]
}
],
"parameter_values": []
}
}
}
}
]Migrate ABAC BETA implementation to custom token API
To generate a JWT token with ABAC security rules, ThoughtSpot recommends using the /api/rest/2.0/auth/token/custom API endpoint. If your ABAC implementation uses /api/rest/2.0/auth/token/full or /api/rest/2.0/auth/token/object API endpoint, please switch your workflow to the
/api/rest/2.0/auth/token/custom API.
This document assumes that you are currently using the /api/rest/2.0/auth/token/full or /api/rest/2.0/auth/token/object for ABAC token generation, and provides instructions to migrate your ABAC implementation to the /api/rest/2.0/auth/token/custom API endpoint.
Key changes to note🔗
Note the following key changes introduced in the GA rollout of the ABAC feature:
- API endpoint for ABAC token generation
-
Use the custom token endpoint (
/api/rest/2.0/auth/token/custom) API endpoint to generate ABAC tokens. - User properties
-
In the beta implementation of ABAC token generation with
/api/rest/2.0/auth/token/fulland/api/rest/2.0/auth/token/object, the security attributes are stored in theuser>user_parametersobject. In the ABAC implementation with the/api/rest/2.0/auth/token/customAPI endpoint, security rules are now stored inuser > access_control_propertiesinstead ofuser > user_parametersobject. - persist behavior
-
Note these changes in the security rules persistence behavior:
-
If the
persistattribute was set totruein your current implementation with/api/rest/2.0/auth/token/fullor/api/rest/2.0/auth/token/object, to replicate this behavior after migration, you must set thepersist_optionattribute toREPLACE. -
The default
persist_optionfor token requests to the/api/rest/2.0/auth/token/customAPI endpoint isAPPEND, which appends the new conditions instead of replacing the existing rules. -
To replace the persisted attributes, set
persist_optiontoRESETin your POST API call to/api/rest/2.0/auth/token/custom, and then send another API request withpersist_optionset asAPPEND.
-
- Runtime sorting
-
The token generation workflow with the
/api/rest/2.0/auth/token/customAPI endpoint does not support runtime sorting. If there are any runtime sorting rules applied via JWT tokens generated from the/api/rest/2.0/auth/token/fullAPI call, they will be ignored during migration.
Migration steps🔗
Migrating your ABAC implementation to the custom token endpoint involves the following steps:
Step 1: Build API requests using the custom token endpoint🔗
Use the REST API v2 Playground test and build requests for the /api/rest/2.0/auth/token/custom endpoint.
For more information about the API request and response, see Get tokens with custom rules and filter conditions.
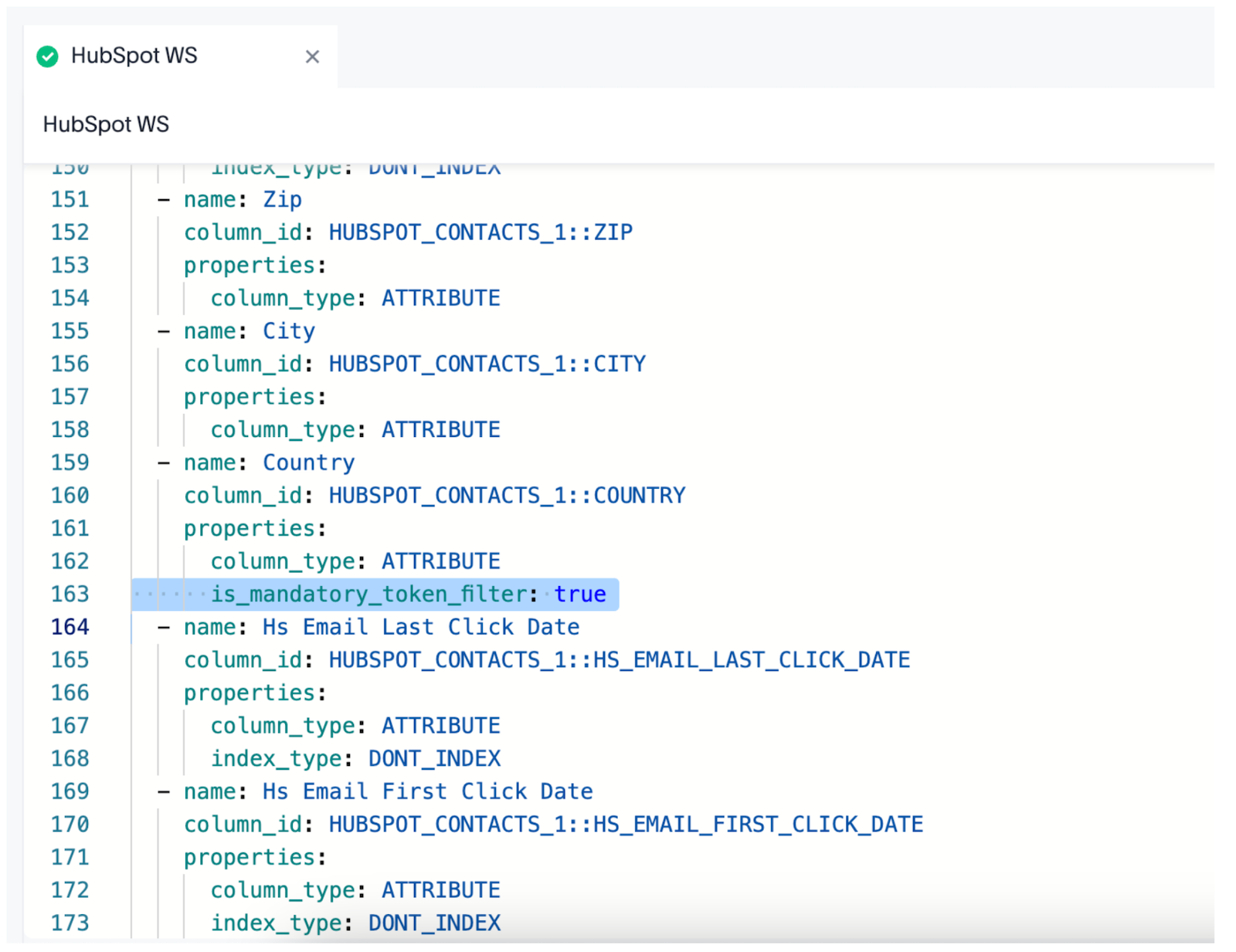
Step 2: Set column flags🔗
In your Worksheet/Model, set is_mandatory_token_filter to true on columns you want to secure. In Worksheets/Models, set is_mandatory_token_filter to true on the columns you want to secure.
Step 3: Switch your token generation workflow🔗
To schedule your migration or validate your ABAC implementation with the custom token endpoint, contact ThoughtSpot Support.
ThoughtSpot allows only one type of JWT API token request workflow at a time, either /api/rest/2.0/auth/token/full or /api/rest/2.0/auth/token/custom. However, after migration and upon successful validation of your token generation workflow with the custom token endpoint (/api/rest/2.0/auth/token/custom), ThoughtSpot strongly recommends that you do not use the /api/rest/2.0/auth/token/full or /api/rest/2.0/auth/token/object API endpoints to generate JWT tokens for ABAC implementation.
Additional resources🔗
-
To learn how to generate JWT tokens with ABAC security rules via
/api/rest/2.0/auth/token/custom, see ABAC via tokens documentation. -
Check the ABAC examples on the ts_everywhere_resources GitHub Repo.